The need to ensure confidentiality has expanded exponentially with the increase of recent Internet usage. For users and enterprises, the reliability and accessibility of their networks have become critical, and the development of secure infrastructure to protect user identity and privacy information is crucial. Internet development and popularity have generated many issues such as cyber theft, hacking, phishing, spamming and many more.
Individuals and companies have migrated their data to a cloud architecture that poses new data protection issues and threats. According to the Cybersecurity Ventures survey, cybercrime exposure could cost 6 trillion dollars a year worldwide by the end of 2021. It further protects networks and processes by recognizing common vulnerabilities and enabling them to take appropriate safeguards.
We have performed both server-side and client-side exploitations to understand the process. We have used the Kali Linux Operating System tool to complete these ethical hacking and penetration testing. In the end, we have proposed mitigation measures and security enhancement to resist hacking attacks. The solution comes from network security applications that perform active port scanning and banner grabbing in order to determine open ports, and the applications / services behind them. Such solutions give instant visibility into the security of your server from the outsider's perspective, by mimicking attacker's behavior.
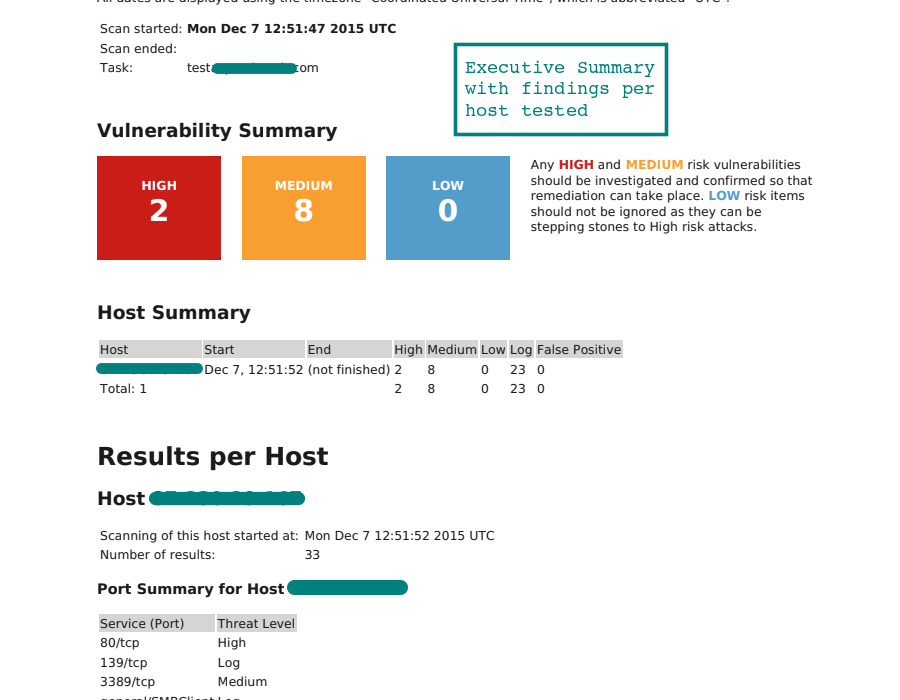
Some solutions gather extended information about the applications and services behind open ports, and also point out potential vulnerabilities which may be exploited. Aport scanis a method for determining which ports on a network are open. As ports on a computer are the place where information is sent and received, port scanning is analogous to knocking on doors to see if someone is home. Running a port scan on a network or server reveals which ports are open and listening , as well as revealing the presence of security devices such as firewalls that are present between the sender and the target. It is also valuable for testing network security and the strength of the system's firewall.
Due to this functionality, it is also a popular reconnaissance tool for attackers seeking a weak point of access to break into a computer. An attacker engages in scanning activity to find vulnerable software versions or types, such as operating system versions or network services. Vulnerable or exploitable network configurations, such as improperly firewalled systems, or misconfigured systems in the DMZ or external network, provide windows of opportunity for an attacker. Common types of vulnerable software include unpatched operating systems or services (e.g FTP, Telnet, SMTP, SNMP) running on open ports that the attacker has identified. Attackers usually begin probing for vulnerable software once the external network has been port scanned and potential targets have been revealed. Ephemeral ports are temporary assignments which are allocated for the source ports of protocol process.
At times, applications which consistently allocate to ephemeral ports are targeted. For example, UDP port 1900 for SSDP has been targeting in the past. Some Operators have deployed UDP port 1900 to their exploited port filtering rules with no customer complaint increase. The key is for exploited port filtering to be deployed and not be blocked by "perceived risk" to customer impact. Each port and exploitability to that port would determine the direction of the filter. For most ports, filtering into and out of the customer would be the best way to minimize risk.
One of the huge mistakes Operators will make in their security profile is the belief that their customers are part of their network and under their control. They then become as much of a threat to the Operator's network as threats from the Internet. Given this, Operators are strongly recommended to view the exploitable port filtering on the egress as part of the tools they use to protect their business from threats which victimize their customers. These cybercriminals often use port scanning as a preliminary step when targeting networks. They use the port scan to scope out the security levels of various organizations and determine who has a strong firewall and who may have a vulnerable server or network.
A number of TCP protocol techniques actually make it possible for attackers to conceal their network location and use "decoy traffic" to perform port scans without revealing any network address to the target. This paper describes an experimental approach to determine the correlation between port scans and attacks. Discussions in the security community often state that port scans should be considered as precursors to an attack. However, very few studies have been conducted to quantify the validity of this hypothesis. In this paper, attack data were collected using a test-bed dedicated to monitoring attackers.
The data collected consist of port scans, ICMP scans, vulnerability scans, successful attacks and management traffic. Two experiments were performed to validate the hypothesis of linking port scans and vulnerability scans to the number of packets observed per connection. Customized scripts were then developed to filter the collected data and group them on the basis of scans and attacks between a source and destination IP address pair. The analyzed data consists of forty-eight days of data collection for two target computers on a heavily utilized subnet.
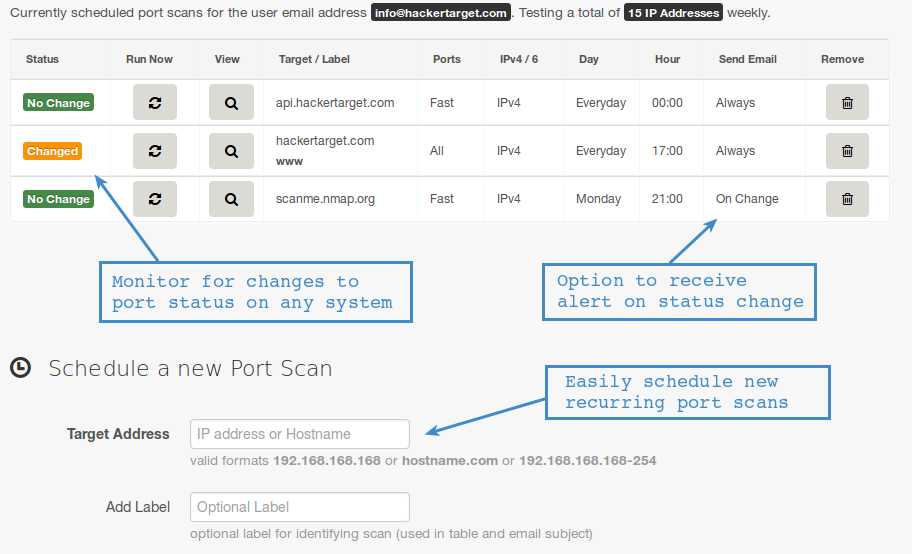
Security across all network ports should include defense-in-depth. Close any ports you don't use, use host-based firewalls on every host, run a network-based next-generation firewall, and monitor and filter port traffic, says Norby. Do regular port scans as part of pen tests to ensure there are no unchecked vulnerabilities on any port. Pay particular attention to SOCKS proxies or any other service you did not set up. Patch and harden any device, software, or service connected to the port until there are no dents in your networked assets' armor.
Be proactive as new vulnerabilities appear in old and new software that attackers can reach via network ports. Some services or applications running on open ports may have poorly configured default settings or poorly configured running policies. Such applications may be the target of dictionary attacks, and, with poorly configured password policies, for example, attackers can identify credentials used by legitimate users.
Furthermore, attackers can use the credentials to log into such applications, steal data, access the system, cause downtime or take control of the computer. Open ports are used by applications and services and, as any piece of code, they may have vulnerabilities or bugs. The more applications and services run using open ports for Internet communication, the higher the risk of one of them having a vulnerability that can be exploited. A bug in one service reachable from the outside may cause it to crash. Such a crash may lead to execution of arbitrary code on the affected machine, exactly what the attacker needs in order to be successful.
As port scanning is an older technique, it requires security changes and up-to-date threat intelligence because protocols and security tools are evolving daily. As a best practice approach, port scan alerts and firewalls should be used to monitor traffic to your ports and ensure malicious attackers do not detect potential opportunities for unauthorized entry into your network. Every logical port is subject to a threat to a system, but some of the commonly used ports receive a lot of attention from cybercriminals.
Cybercriminals use vulnerability scanners and port scanning techniques for identifying opened ports on any system or server. Next, they can identify what kind of services are running and the kind of system being used by the target victim. Here's the list of potential logical ports that are the targets of cybercriminals.
RUCKUS could allow a remote attacker to bypass security restrictions. An unauthenticated remote attacker with network access to port 22 can tunnel random TCP traffic to other hosts on the network via Ruckus devices. A remote attacker could exploit this vulnerability to bypass security restrictions and gain unauthorized access to the vulnerable application. By sending a specially-crafted SNMP SetRequest PDU sent to UDP port 16, a remote attacker could exploit this vulnerability to cause the application to crash. The crash of the unused NTP service causes system instability and may bring down an entire server.
Thus, an attacker can perform successful denial of service attacks on a web server, without even targeting port 80. Behind open ports, there are applications and services listening for inbound packets, waiting for connections from the outside, in order to perform their jobs. Security best practices imply the use of a firewall system that controls which ports are opened or closed on Internet-facing servers.
Additionally, security best practices advise that ports should be open only on a "need-to-be" basis, dictated by the Internet communication needs of applications and services that run on the servers. The goal behind port and network scanning is to identify the organization of IP addresses, hosts, and ports to properly determine open or vulnerable server locations and diagnose security levels. Both network and port scanning can reveal the presence of security measures in place such as a firewall between the server and the user's device.
The scanner then terminates the session without establishing a connection. If the port is closed, it responds with an RST packet, indicating that it cannot be accessed. If the port is located behind a firewall, the request does not generate a response at all.
This is the most common scanning method because it does not require an established connection and is not logged by most simple event-tracking tools. On the other hand, SYN scanning requires superuser privileges on the device that sends the requests and which might not belong to the attacker. All networks are secured by one firewall on the perimeter of the network, and this firewall is configured to permit HTTP and SMTP traffic to pass through. Other application traffic is forced to use a secured tunnel to pass through the network.
Of course, the perimeter firewall is configured to monitor the traffic, and a log is kept for analysis. Internal network is built using Ethernet segments to reflect the infrastructure of the organization. IP network segments are then superimposed on the Ethernet segments. Each of the IP segments is connected to the layer-3 switch, thus further protecting each IP segment from an external attack.
The IP traffics from the layer-3 switch are directed to pass through a Demilitarized ZONE before it enters the perimeter router. The nodes in the DMZ are DNS, SMTP, and HTTP servers, which are permitted for both inbound and outbound traffic. The attacker would scan the ports on the perimeter firewall and look for open ports on the firewall. The firewall would have the ports such as 80 and 25 (well-known) open for Web and email services. The goal of the attacker is to find which ports in "listen," "wait," or "closed" state.
Businesses can also use the port scanning technique to send packets to specific ports and analyze responses for any potential vulnerability. They can then use tools like IP scanning, network mapper , and Netcat to ensure their network and systems are secure. This study assessed the security of the U.S. state e-government sites to identify opportunities for and threats to the sites and their users. The study used a combination of three methods – web content analysis, information security auditing, and computer network security mapping – for data collection and analysis.
The findings indicate that most state e-government sites posted privacy and security policy statements; however, only less than half stated clearly what security measures were in action. Third, although the sites had most of their internet ports filtered or behind firewalls, all of them had their main IP addresses detected and their port 80/tcp open. The study discussed the threats and opportunities and suggested possible solutions for improving e-government security. The main drawback for deploying active exploit filters is the blocking of scanning by Whitehat organizations. There are groups who will scan for vulnerable systems and provide you reports. Blocking an active exploit port will also block the whitehat scanning.
In that case, it might be worth considering setting up a "vulnerable port scanning system" in your network to find customers which might be a vulnerability. Infected customers cause unnecessary damage, generates calls to the Operator's help desk, pose a risk to the Operator's other customers, and increase the chance of damage to the Operator's core infrastructure. The Operator will always be exploring options to reduce the business risk to their infrastructure and their customers. This is why the risk reductions gained by the anti-spoof/source address validation filters AND anti-exploit port filters are critical to the Operator's business.
Deploying Exploitable Port filters on the customer edge minimizing the risk to and from the customers . Applying these same filters to the Operator's network (protecting the Operator's staff and infrastructure) adds additional risk reduction. Finally, monitoring the volume of exploitable port traffic on the peering edge keeps a temperature to the Threat Actor's interest in the ports. This tool can test open ports, but it can also conduct a full recon of your network, assisting you in the identification of any potential security risks. An open port scanner tool or open port check tool can only afford you a small, limited picture of your network, system, and processes.
That's why Engineer's Toolset also features an IP network browser. With the port scanner, this utility will sweep IP ranges, identifying devices, UDP and TCP services. This will afford you visibility of what services are reachable and which devices are connected to the network. Some malicious software acts as a service, waiting for connections from a remote attacker in order to give them information or control over the machine.
In the bounce scan, the attacker would attempt to fool or mislead the victim into believing that the attack originated from a different source IP address, often known as the distributed denial-of-service attacks . Such an attack would make it difficult to trace the attacker's IP address. Most commercial Internet sites such as Yahoo, Google, Microsoft, and others support proxy services so that all Web traffic can be directed to a single server for filtering as well as caching to improve performance. We have seen cases of DDOS in spite of the proxy servers' setup to protect the networks. This paper provides a Common Vulnerability Scoring System metric-based technique for classifying and analysing the prevailing Computer Network Security Vulnerabilities and Threats . The problem that is addressed in this paper, is that, at the time of writing this paper, there existed no effective approaches for analysing and classifying CNSVT for purposes of assessments based on CVSS metrics.
The authors of this paper have achieved this by generating a CVSS metric-based dynamic Vulnerability Analysis Classification Countermeasure criterion that is able to rank vulnerabilities. The CVSS metric-based VACC has allowed the computation of vulnerability Similarity Measure using the Hamming and Euclidean distance metric functions. Nevertheless, the CVSS-metric based on VACC also enabled the random measuring of the VSM for a selected number of vulnerabilities based on the [Ma-Ma], [Ma-Mi], [Mi-Ci], [Ma-Ci] ranking score. The authors have also proposed high-level countermeasures of the vulnerabilities that have been listed.
The authors have evaluated the CVSS-metric based VACC and the results are promising. Based on this technique, it is worth noting that these propositions can help in the development of stronger computer and network security tools. As ethical hackers we can use common ports such as HTTP port to bypass the firewall as normally, the HTTP port is enabled by default in the firewall. Nmap is a network exploration tool, and it will be used to perform port scanning and determine the targeted operating system . There are two types of exploit can be done such as client-side and server-side exploit. Many attacks are low and slow, creating command and control channels that allow them to exfiltrate more data and remain undetected for longer periods of time.
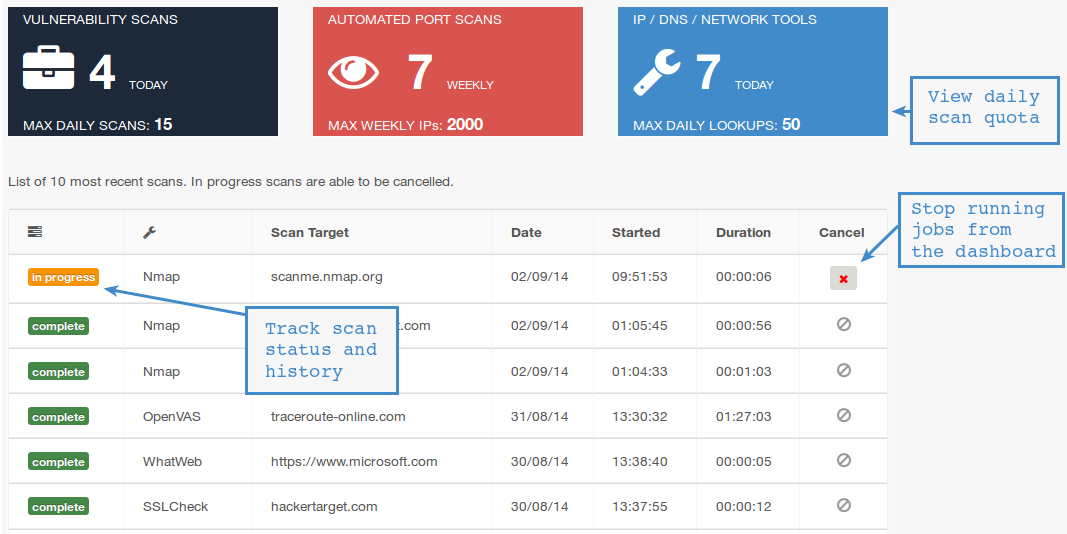
The complexity of networks, and the multitude of open ports across an organization make identifying threats increasingly difficult. The simplest, most straightforward, and costliest approach is a reactive stance where you wait for something to happen and fix it. The best solution is to proactively scan and analyze the network infrastructure. Tenable.io enables analysts to compare known open ports between scans. New active ports and vulnerabilities can be detected, avoiding potential blind spots where new services are installed or enabled.